In This Issue
Training: Police and Military Criminal Investigators, Crimes Against Women Conference
Operations: Support to Oklahoma
Events: Expedition XV Tampa
OSINT Tradecraft: 10 Deadly Sins of OSINT Analysis
Who We Are
The Skull Games Task Force employs Open Source Intelligence to IDENTIFY sexual predators and their victims, enabling law enforcement to INTERDICT the cycle of abuse. Our mission is to liberate survivors and EMPOWER them with the opportunity for a life of hope, healing, and freedom. The Task Force provides direct support to law enforcement through small teams or as a massive expedition, bringing together the collective capability of more than 400 elite volunteers. This counter-sexual exploitation offensive leverages considerable expertise and resources to fight human trafficking and sexual exploitation. With us as the HUNTERS, we get into the heads of predators, in our own “SKULL GAME”…
Operations Summary – May 2025
by Olinda Cardenas
- Law Enforcement operations supported: 5
- Sex Predators Arrested: 16
- Victims Recovered and offered services: 19
- People trained in Counter-Trafficking: 28
Recent Operation Summary:
The Skull Games team had the honor of supporting a targeted operation in Tulsa, Oklahoma, alongside dedicated law enforcement partners. This collaborative effort resulted in the recovery of 15 victims of human trafficking, including a missing child from a neighboring state. Six suspects were taken into custody, and dangerous narcotics were seized from the scene. The success of this operation serves as a testament to what can be achieved when agencies and organizations unite with a shared purpose.
To close out the month of May, Skull Games was proud to support District 27 and the Violent Crime Task Force in a successful operation targeting online predators in Coweta, Oklahoma. This joint effort resulted in seven arrests—including three business owners and a federal agent—and, most importantly, the recovery of two victims, now connected with critical support services. We’re grateful to all the agencies involved in delivering justice and restoring hope to those affected. While predators were being cuffed in Coweta the team was also in Shawnee, OK, delivering our Advanced Human Trafficking Course to law enforcement professionals from across the region. As that class ended, a simultaneous operation launched in Shawnee. As a result of that operation, 2 predators were arrested, 1 sex trafficker arrested, 1 victim of sex trafficking recovered, and 1 additional victim identified.


Training Provided – May 2025
by Olinda Cardenas
The Skull Games training team kicked off a busy month for May in Lubbock, TX, delivering sessions with participants from DPS Lubbock and Abilene, Lubbock County SO, Lubbock PD, LISD PD, Lamesa PD, and Motley County SO. From there, they headed to Fort Leonard Wood, MO, to train members of the Army and Marine Corps Criminal Investigation Divisions, as well as the Coast Guard Investigative Service. The expert training provides more equipped allies in the war on human trafficking, not only in law enforcement but our armed services.
The team then joined the Conference on Crimes Against Women in Dallas, an internationally attended event, where the team led impactful sessions on OSINT in investigations, working with interpreters in gender-based violence cases, and addressing vicarious trauma and mental health for investigators.
The team closed out the month with one final training and operation near Oklahoma City, in Shawnee. It’s been an incredible month for the Skull Games training team—full of connection, collaboration, and continued learning.
Events – May 2025
Expedition XV: Ybor City
by Olinda Cardenas
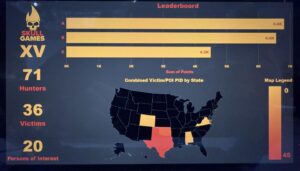
Like many of my fellow Skully volunteers, I made my way to Tampa, FL for TF Expedition XV—an experience that was not only impactful, but truly unforgettable. From the moment I walked in, I felt a mix of anticipation and humility. I didn’t know exactly what to expect, but I knew I was surrounded by people who genuinely cared about this work. Over one powerful weekend, 71 OSINT analysts—both in person and remote—came together with a shared mission: to identify victims of human trafficking and the people exploiting them. Together, we helped identify 36 victims and 20 persons of interest across five states.
One of my favorite moments was collaborating with my teammates. We quickly built a rhythm, sharing screens, bouncing ideas, following leads, and by the end of the session, we were successfully identifying victims and earning points for Team A. That rush of discovery, mixed with a sense of responsibility, was unlike anything I’ve felt before.
What surprised me most wasn’t just the complexity of the cases, but how naturally relationships formed throughout the weekend. We were all there for the same reason, and that shared purpose created a deep sense of trust and connection, something rare in volunteer environments. Meeting members of the Skull Games Solutions team, survivors, and leaders I’ve looked up to was incredibly humbling and motivating.
If you’re thinking about joining an in-person TF Hunt, do it! Being in a room full of like-minded, mission-driven people reminded me why I chose this path in the first place. It’s one thing to sit behind a screen doing good work, it’s another thing entirely to feel the collective heartbeat of a team making a difference in real time.
To round out the events for May, we send a huge congratulations to those who earned their OSC certification during the TF Hunt weekend! Another heartfelt thank you to the team at the OSMOSIS Association for making the exam accessible to volunteers, and a final special shoutout to Cynthia Hetherington for joining us in person. It made it an incredible honor to achieve this milestone with you there—it truly made the moment unforgettable.

OSINT Tradecraft: Professional OSINT Research
by Tom Phelan
OSINT Tradecraft: Top 10 Analytical Pitfalls
If you’ve ever spent hours chasing OSINT leads, only to realize you were chasing a dead end, you’re not alone. OSINT analysis can make us feel like Alice, lost in internet Wonderland, but with way more rabbit holes to fall into. We sometimes follow (and stay on) the wrong path out of pride, laziness, or confusion. Mistakes are part of the process and being human, but they often can be avoided. The best analysts combine analytical tradecraft, doctrine, and self-awareness to avoid common pitfalls that can waste time, skew conclusions, or even harm the people we’re trying to help. This month’s tradecraft lesson outlines the Top 10 Analytical Pitfalls in OSINT: what they are, why we fall into them, and how to avoid them.
Why We Get It Wrong, The Psychology Behind OSINT Pitfalls
The human brain is hardwired for pattern recognition, a trait that put us at the top of the food chain. This trait is ingrained in our DNA, so it becomes hard to control and can cause us to leap to conclusions based on incomplete data. Some errors that can occur in the analytical part of our psyche include:
Confirmation Bias: favoring evidence that supports what we already believe
Anchoring: placing too much weight on one data point
Cognitive Dissonance: ignoring contradictory data to avoid discomfort
Recognizing these tendencies is the first step in mitigating them. They are also the driving force behind the top ten mistakes we make as OSINT analysts.
Top 10 Analytical Pitfalls in OSINT
Think of these as the ten commandments of what not to do as an analyst, or the ten deadly sins.
- Bias
What it is: The original sin of intelligence analysis. Confirmation bias means favoring data that confirms your assumptions. We may give more weight to information we like and even be more likely to forget information that doesn’t fit the narrative we want.
Example: You want to find a human trafficker, so you find one. A victim is identified online and mentions a boyfriend. You label him a trafficker based on vague references, while ignoring evidence that you have the wrong person of interest.
Avoid it: Actively seek disconfirming evidence using a structured methodology. Then get peer reviews to challenge your assumptions. At Skull Games, we never work alone so we can always get at least one unbiased pair of eyes on a problem.
- Fixation
What it is: Also known as anchoring, early fixation, or satisficing. It’s the tendency to get attached to the first plausible data point, connection, or piece of evidence. We want to believe things are fast and easy because we’re good at what we do. But rarely is your first lead a jackpot.
Example: You identify an image that you think could be your person of interest. You waste hours working on this lead before realizing it’s not who you were looking for.
Avoid it: Keep the scope of your research broad in the beginning. Follow a collection plan that will give you a data set to analyze before making a hypothesis. Set standards for confirming your hypothesis i.e. image plus location plus behavior equals confirmation. Then develop other hypotheses, because the detail you’re banking on could be a deception like a burner account, bot, or decoy.
- Trust
What it is: Believing that what’s online is current, accurate, or genuine. People, especially criminals, have countless reasons to deceive you online and countless ways to do it. Social media is, hands down, the best place to lie about yourself. On top of that, the internet itself is unreliable, filled with outdated, corrupted, or uncached data.
Example: You find an escort ad with a picture, phone number, and city. You assume it’s a good lead and incorporate it into your assessment. Turns out the page was actually a phishing attempt that copied the victim’s picture from somewhere else.
Avoid it: Trust no one. Assume everything you see on the internet is a lie. Verify everything, check timestamps, metadata, WHOIS, EXIF data, and corroborate across platforms. For that specific example, Virustotal.com and virustotal API are also good resources for checking website legitimacy.
- Overreliance
What it is: Relying too much on your tools. OSINT tools are platforms for information collection and organization, but they don’t do your job for you. Automation and AI can’t replace critical thinking.
Example: Accepting an AI facial recognition or geolocation match without checking for false positives, manipulation, or error.
Avoid it: Understand how your tools work. They help sort through big data, but it’s up to you to verify it. Always manually check and cross-reference results using multiple sources.
- Tunneling
What it is: These are the rabbit holes you and Alice fall into. Tunnel vision is getting too locked into one data point, narrative, or hypothesis. It’s common and usually harmless, other than wasting a lot of time. Often caused by pride in a lead you’re following, you get hyper focused and miss the big picture.
Example: You’re tracking a trafficker through Instagram, and realize they are currently incarcerated. You get attached to the idea that they are running their trafficking ring from prison, and you miss that they delegated their operation to an associate.
Avoid it: You don’t want to reach your deadline and realize you have a great understanding of one aspect of an investigation but don’t know their basic profile or pattern of life. Periodically zoom out. Use link analysis tools to map a full digital footprint, not just the info you are comfortable with. This is especially hard for analysts with certain specialties. A cyber expert may overwork the network signature and a threat finance expert will follow the money. Use your gifts but try to be well rounded.
- Patterning
What it is: Our brains crave patterns. It’s how our caveman ancestors avoided lions and poison berries. Unfortunately, this can lead us to seeing connections where none exist, often due to pressure, pride, or emotional investment.
Example: Seeing similar identifiers and assuming they are connected without confirmation. For instance, the username you have for a subject is “alex1992,” so you assume “alex_1992” and “alex92” are the same account holder on similar platforms.
Avoid it: Require at least two independent matching data points, like phone number and behavior. Avoid assuming intent based on coincidence.
- Mirroring
What it is: We can only analyze from our own perspective, so we assume the subject thinks, acts, or communicates like us. This is a common fallacy that can only be overcome with research and an open mind. You may assume that a criminal should have as much compassion as you, or that a victim would be motivated to resist their oppressor. Many of the situations you investigate are more complex than what you see on the surface.
Example: Lack of research in human trafficking investigations often leads to misreading or missing high-context cues, like crime-related emojis or slang, because they don’t match the terms you’re familiar with.
Avoid it: Try to see things from the perspective of others. Study regional and cultural norms. When in doubt, consult experts. To understand trafficking, you might read books like Pimp: The Story of My Life by Iceberg Slim or study survivor stories.
- Overload
What it is: Drowning in so much data that you lose track of what matters. Big data tools are great, but only if they include proper management and analysis functions. Otherwise, you scrape the entire internet and end up no closer to finding the detail you needed. In OSINT, you rarely want big data, you want the right data.
Example: You scrape 3,000 social media data points potentially relating to a person of interest, including posts, photos, videos, bios, comments, friends, and likes. You spend several hours searching for evidence but barely make a dent and are no closer to a functional analysis.
Avoid it: Define the scope of your investigation up front and create a thoughtful research plan. You can use tagging systems for data management, OSINT notebooks like Hunchly or Obsidian. and regularly purge irrelevant data.
- Violation
What it is: Violating platform Terms of Service, local laws, or ethical norms during data collection.
Example: You use a fake LinkedIn profile to connect with a suspected trafficker, violating LinkedIn’s TOS. That data is later used in a legal case, but the entire chain of evidence is thrown out due to improper collection.
Avoid it: Know the law and follow it. With hard work you can almost always reach a solid assessment with passive collection alone. By taking legal and ethical risks not only do you potentially jeopardize and investigation but you may also alert a suspect that they are under scrutiny. Don’t take the risk, create sock puppets unless you need them and you’re properly authorized.
- Laziness
What it is: Cutting corners in data collection, verification, or analysis because you’re tired, rushed, or just not in the mood to do the hard parts. This often shows up as accepting the first result that looks “close enough,” skipping corroboration, or failing to follow up on leads.
Example: You run a phone number search and get a return on a name and address. You run with the idea that the listed name is a trafficker, even though you find no incriminating evidence.
Avoid it: Try to break your own theory. If you’re wrong, find out early. Use structured techniques to force objectivity. It’s far more work to redo an investigation than to get it right the first time.
Practical Tools to Avoid Mistakes
Layered Verification: use two or more independent indicators, such as phone number and image
Chain of Custody: document what you ruled out and why
Team Reviews: work with others, as peer review often exposes blind spots
Stoplight Confidence Scale:
- High Confidence, two or more confirmed sources
- Moderate Confidence, incomplete but promising
- Low Confidence, unverified or suspect
Final Thought: Trust the Process, Not Just Your Gut
Being wrong is part of being human. Staying wrong out of pride, fatigue, or pressure is what leads to real failure. The theme of these pitfalls is not that you need to be an expert in analytical tradecraft, tools, or other subjects, it’s that you need to be disciplined. Don’t let internal struggles or external pressures get in the way of what you know you need to do. Whether you’re working a live trafficking case or building an identity map, the best OSINT tradecraft is rooted in humility, curiosity, and disciplined skepticism. When in doubt, take a break or get a second set of eyes.
Upcoming Events
- Task Force Expedition XVI | August 1st – 3rd | Austin, TX
- Task Force Expedition XVII | October TBD | Arlington, VA
Skull Games Links
- Social Media: Follow Us Linkedin Facebook Insta Twitter
- Donations: Support Us
- Law Enforcement: Partner With Us
- Volunteer: Join Us
About the Author

Tom Phelan is an active-duty U.S. Army Intelligence Officer with over five years of experience in OSINT and a dedicated volunteer for Skull Games Task Force.

Olinda Cardenas is a former crime scene investigator turned cybercrime enthusiast. She specializes in OSINT and financial crime investigations and is a dedicated volunteer with Skull Games




