Who We Are
Skull Games operates on a global scale to identify predators, working tirelessly to protect the vulnerable and break the cycle of abuse for future generations. The Skull Games Task Force utilizes Open-Source Intelligence (OSINT) to identify sexual predators and their victims, creating actionable leads that law enforcement can use to interdict the cycle of abuse. Our mission empowers survivors, providing them with the opportunity for a life of hope, healing, and freedom.
Throughout the year, the Task Force offers direct support to law enforcement through small, specialized teams. During periodic events, the Task Force surges, bringing together the collective expertise of vetted volunteers from across the United States. This comprehensive counter-sexual exploitation offensive leverages the experience, capabilities, and resources of our team, working in collaboration with our trusted partners to fight back against human trafficking and sexual exploitation.
Task Force Operations in January 2025
- Predators & Victims Identified: 68
- Predators Arrested: 23
- Victims Recovered: 4
- Hunters Trained: 27
- Active LE Investigations Supported: 10
Recent Operation Summary:
- Skull Games supported a recent operation in Texas where twenty buyers were interdicted for solicitation and two traffickers were arrested for promotion of prostitution.
News & Events
TF Expedition XIV: Summit Point
In January 2025, the Skull Games Task Force reunited for Expedition XIV to track Persons of Interest (POIs) connected to human trafficking, supporting our law enforcement partners. This effort saw forty-six victims and seventeen POIs located by our fifty-eight skilled OSINT professionals, making the expedition a resounding success. Volunteers from across North America braved the winter conditions in West Virginia, embodying the strength and commitment of the Skull Games community.

The expedition began with a fun, albeit unconventional, team-building exercise: advanced firearms and tactical driving training provided at the Summit Point Training Facility. Skullys conducted shooting drills with handguns, then barricade breaching and precision immobilization technique (PIT Maneuver) in vehicles, and much more valuable training. This training ensures that our team is equipped with both online and offline skills, ready to make an impact in every facet of the fight against trafficking.
Saturday and Sunday of the Expedition are when the hunters go to work. From early morning until night, all participants provide exceptional effort, investigating the murky internet underworld of human trafficking. The Skull Games family always seem to enjoy themselves when they can unite as a community, despite the sometimes somber nature of their work. There is also some good-spirited competition at the events between teams. The winning team for Skull Games XIV was Team Alpha.

Task Force members Dallas Knight (pictured above) and Sylvia Vadney were on the winning team and Sylvia shares her experience, “Skull Games XIV Summit Point was my fourth hunt. Personally, the hunts in many ways are the same to me. Exciting every time, when you find a bread crumb that could lead to an identity. Exhilarating every time you find an identity, knowing that the efforts you and your team put into the case could be the information that assists law enforcement in helping a victim or arrest a predator. Being part of a group of people from various backgrounds, experiences, and ways of working, whether law enforcement, military, the private sector or my favorite people, past victims, is so humbling, moving, and motivating. Each hunt I meet new people, learn new techniques, and gain new memories of those we help.”
When asked what made Skull Games XIV: Summit Point unique and how her team achieved such success, Sylvia credited her best friend and team leader, Dallas Knight. “With our team lead pushing and directing us, along with our diverse expertise, our trio became a rockstar group.,” Sylvia said. Dallas in turn attributed their success to the team’s, “ability to stay focused, constantly communicate with one another, and know when to pivot in a more productive direction. The three of us brought a very unique and dynamic skill set to the table. We discussed this in the first 10 minutes of being together as a team and continued to leverage our strengths throughout the weekend.” Dallas has been a Task Force Member since Skull Games III. She left a position as an intelligence analyst in 2014 and was desperate for an opportunity to once again leverage the skills she mastered for a noble cause. She now uses those skills to make an impact on our communities and to mentor all the promising talent that is new to the community.
Joining them was Rikki Wiley, who was on her first expedition but immediately synchronized with her team and added significant value. Rikki was surprised by how inviting the Skull Games community was and at the level of comradery within the Task Force. Rikki felt validated that she was able to use her OSINT skills in such a way that could potentially save the life of a stranger.
The teamwork of the three led to them being able to effectively identify and locate victims and POIs. Sylvia remarked that there is no better feeling than having that level of success in their mission because sometimes you just are not able to identify the necessary evidence. She also appreciated the success of this mission was not only due to the hard work of our volunteers but also the support of our sponsors, who demonstrate their genuine commitment to the cause.

Skully University
Ritu Gill, President of OSMOSIS Association, took the time to provide this month’s Skully University training in a segment entitled ‘Unveiling Deception: Identifying a Catfish.’ What is a catfish? Ritu defines it simply as, “an individual who presents to be someone else online.” This could be someone disguised as a completely fictional persona or impersonating someone’s real online identity. Why is this important to OSINT professionals? When conducting research, OSINT professionals need to be sure that the information they are analyzing is verifiably about the correct person of interest. This is especially true for the SGTF objective, as the material we gather must be as precise as possible before it can be presented to law enforcement for action. Most OSINT specialists understand how to conceal their identity for security reasons; therefore, it is reasonable to think that experienced criminals would learn some of the same techniques. Ritu taught SGTF members to identify the ‘red flags’ of a possible catfish.
Some of these red flags include few social media posts, few friends, and suspicious behavior such as pursuing personal details that could be used for extortion or identity theft. One way to combat possible catfish are reverse image searches. Catfish may be using stock images or internet personalities as their profile, and a reverse image search can tell you if that image is available somewhere else on the internet. Another option is the ‘Fake News Debunker’ by InVID and WeVerify. The Fake News Debunker is a browser extension that allows you to right-click and open a tool suite for analyzing suspicious material.
This technique, and others taught by Ritu, can also be applied to the Skull Games counter human trafficking mission. For example, reverse image search options like Pimeyes, can often identify a possible victim in other places they may be exploited under different names and phone numbers by matching their picture to other advertisements or profiles. Trainings and collaboration with industry leaders is what makes the SGTF, through the Skully U platform, such a professional and expert community. We thank Ritu Gill for her persistent commitment and support to Skull Games.
OSINT Tradecraft: OSINT Automation with Python 101
We talked last week about how using Python for OSINT is a fantastic way to streamline efficiency and it is totally free! In some cases, your investigation may deal with a huge amount of data. For that, Python projects help you scrape through all that publicly available information in much larger batches. Python is a great tool for automating repetitive tasks, allowing you to spend more of your time analyzing your data and less time waiting for websites to load. I know coding sounds very technical and daunting, but you do not need to be a super nerd to figure this out. With help from code repositories, AI code generators, and your friendly neighborhood Skull Games Task Force, you too can master the basics of Python. If you work through this guide, you will already have a few of the best simple OSINT Python projects set up in your tool kit forever.
In this guide, we will show you how to set up development environment, how to generate code based on the tool you want, and how to execute the projects for your tailored requirements. You can work with any Python programming tool but for this I will be talking about the major free ones: Visual Studio Code (VS Code) by Microsoft is what I use, and from Jupyter, Jupyter Notebook or JupyterLab are great options. We will also walk through setting this up on different operating systems—Windows, macOS, and Linux—so you can get started no matter what platform you are using. Let’s start with the setup:
Lesson 1: Setting Up Your Environment
- Install Python
- Windows: Download Python from org, and during installation, make sure to check the box that says, “Add Python to PATH.”
- macOS/Linux: Python is often pre-installed, but if you do not have it, install it via your terminal. Terminal is a program that provides a text-based interface (command line) for interacting with the operating system. On Mac is just called “terminal” and on Windows it is called “command prompt.” Search for it in your computer’s start menu.
- macOS: Use Homebrew (macOS packet manager) and enter brew install python
- Linux: Use the package manager for your distro on Ubuntu and enter sudo apt install python3
- Install an IDE: IDE is an integrated development environment, which is software that helps you develop code. Two free options for developing your Python code are VS Code or Jupyter.
Virtual Studio Code
- Download from VS Code’s website.
- Open VS Code, and install the Python extension:
- Press Ctrl/Cmd + Shift + X to open Extensions.
- Search for “Python” (by Microsoft) and hit Install.
Jupyter
- Install by opening your computer’s terminal
- Use ‘pip’, Python’s packet installer, to install Jupyter Notebook by entering pip install notebook or install Jupyter Lab with pip install jupyterlab
NOTE: pip should have come with Python but if not get it here: https://pip.pypa.io/en/stable/installation/
- Start Jupyter by entering jupyter notebook or jupyter-lab in your terminal and hit enter.
- Install Required Libraries: You will need a few Python libraries to perform OSINT tasks. Open the terminal (or a Jupyter notebook cell) and install them by running:
pip install requests beautifulsoup4 pandas whois python-whois
- Set Up Your Workspace: Create a folder for your OSINT projects (e.g., “OSINT_Projects”) to keep everything organized. Open this folder in your chosen development tool.
Lesson 2: Automating OSINT Tasks
Now, let’s dive into the Python projects. We are going to create some .py (Python) files which will tell your computer how to automate your usual OSINT tasks. Executing these python codes in your development environments will be used, in these examples, to check your current IP configuration, extract metadata from images, and look up domain registry information.
- IP Checker
What It Does: Tells you what your IP and location is.
Use Case: This is a great, simple one. As a point of good OSINT tradecraft, you should always check your IP before you get going to make sure your VPN is working. I used to do it through a website because I use a virtual desktop. This way is MUCH faster.
Code Example:
import requests
url = “https://ipinfo.io/json”
response = requests.get(url)
if response.status_code == 200:
data = response.json()
# For this example, we’ll print out the IP and city (no real ‘name’ here)
print(f”IP Address: {data[‘ip’]}”)
print(f”City: {data[‘city’]}”)
print(f”Region: {data[‘region’]}”)
print(f”Country: {data[‘country’]}”)
else:
print(f”Error: {response.status_code}”)
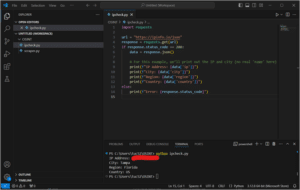
Paste the code into VS Code, save as ipcheck.py, then go in terminal and run python ipcheck.py
Should look something like this (and yes it worked but you can’t have my IP):
- Metadata Extraction from Images
What It Does: Extracts metadata from image files (like EXIF data).
Use Case: Analyze photos for time stamps, GPS locations, and creator information. Yes, you could right-click a photo, go to properties, and details to find this. But sometimes you have quite a stack to go through. With this simple code, you can extract data from many photos at once.
Code Example:
import os
from PIL import Image
from PIL.ExifTags import TAGS
# Folder where your files are stored (use raw string to avoid escape issues)
directory = r”C:\Users\tuc52\OSINT\photos”
# Function to extract EXIF data from an image file
def extract_exif(image_path):
try:
image = Image.open(image_path)
exif_data = image._getexif()
if exif_data is not None:
print(f”Metadata for {os.path.basename(image_path)}:”)
for tag_id, value in exif_data.items():
tag = TAGS.get(tag_id, tag_id)
print(f”{tag}: {value}”)
else:
print(f”No EXIF metadata found for {os.path.basename(image_path)}”)
except Exception as e:
print(f”Error reading {os.path.basename(image_path)}: {e}”)
How to Run in VS Code:
- Create a folder called photos and drop in some image files.
- Save the script as metadata.py. Open the terminal and run python metadata.py
It should look like this:
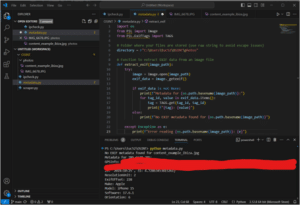
The reason the GPS info is redacted is because I used a stock photo and a personal vacation photo to test. Now, I need to talk to my wife about how to remove Exif data from her iPhone pictures.
- Domain Lookup
What It Does: Domain Information Lookup using the free whois API. This script can fetch details about a domain name, such as the registrar, creation date, and expiration date.
Use Case: Let’s say your person of interest might be the owner of a website or business. With the website URL you can often find information about who owns or registered the website with a domain check.
Code Example:
import whois
def get_domain_info(domain):
try:
domain_info = whois.whois(domain)
print(f”Domain Information for {domain}:”)
print(f”Registrar: {domain_info.get(‘registrar’, ‘N/A’)}”)
print(f”Creation Date: {domain_info.get(‘creation_date’, ‘N/A’)}”)
print(f”Expiration Date: {domain_info.get(‘expiration_date’, ‘N/A’)}”)
print(f”Name Servers: {domain_info.get(‘name_servers’, ‘N/A’)}”)
print(f”Country: {domain_info.get(‘country’, ‘N/A’)}”)
except Exception as e:
print(f”Error fetching information for {domain}: {e}”)
domain = input(“Enter a domain name (e.g., example.com): “)
get_domain_info(domain)
How to Run in VS Code:
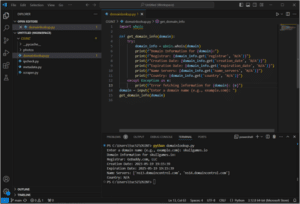
- Create a new file ‘domainlookup.py’ in VS Code, paste the code.
- Go to the terminal and run: py
- Type in your target URL when prompted.
Bonus Lesson: Get coding help with AI
If you have any trouble getting the code to run properly or want to add even more functionality you can use your OSINT skills and google it. Or even easier use one of the many great AI chatbots available for help. If you are getting an error simply type the code and error code into something like ChatGPT. For example, let’s say we want to get more functionality out of our domain lookup tool. I asked ChatGPT if I could add something to the script that would let me query many domains at once. ChatGPT provided an updated code that allows us to have an even more efficient program.
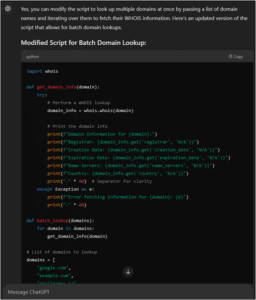
Give a couple of these OSINT python projects a try. Maybe you hate it, or maybe you have fun and become a Python addict. If you commit to the practice, you will find that you are becoming a more efficient OSINT professional and are able to tailor more advanced Python projects to your personal needs. There is a whole community for these projects, and with some practice maybe you move on to some more complex projects like programmatically identifying misinformation, doing big data cleanup, or utilizing OSINT docker API’s. Sky is the limit.
Upcoming Events
- SANS OSINT Summit, Feb 24-25, Arlington, VA
- TF Expedition XV, NTS Ybor City, Tampa, FL: May 2025
Skull Games Links
- Social Media: Follow Us linkedin facebook insta twitter
- Donations: Support Us
- Law Enforcement: Partner With Us
- Volunteer: Join Us
About the Author




